🔍 Splunk Integration & SIEM Testing
In this lab, I integrated Splunk into my home network to simulate a Security Information and Event Management (SIEM) solution. Splunk was used to collect, index, and analyze log data from both Windows Server and Windows 10 endpoints within my Active Directory environment.
Splunk Installation and Setup
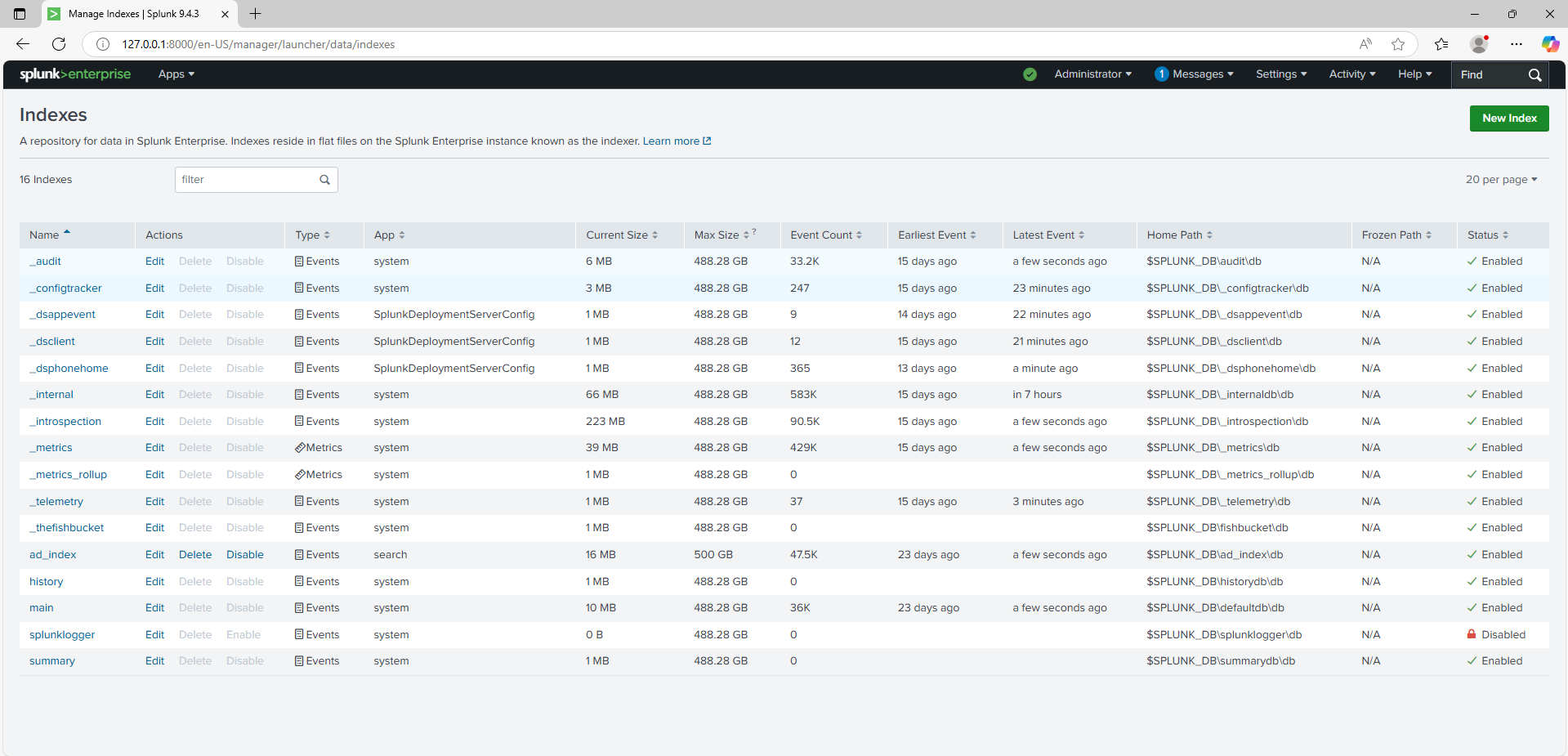
I installed Splunk Enterprise on the domain controller machine and configured the Universal Forwarder to capture log data since the DC is the targeted machine in this simulation.
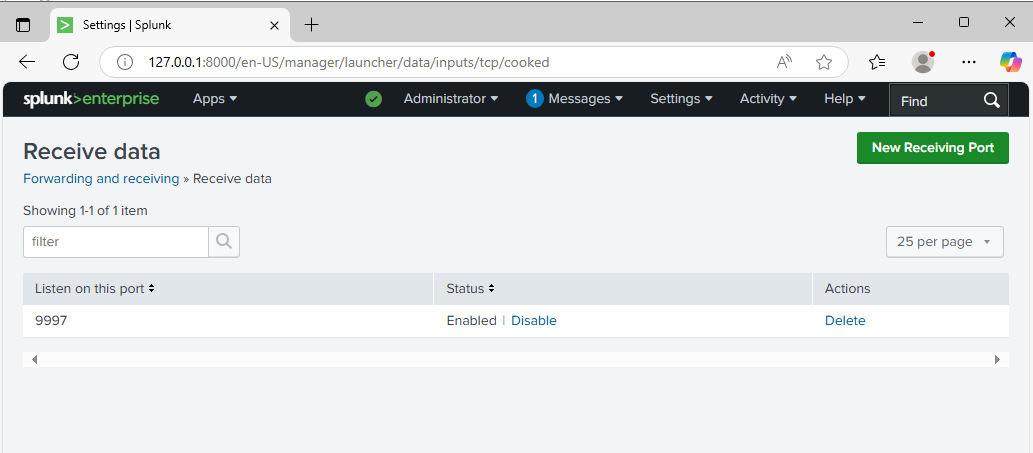
The forwarders were set up to send Windows Event Logs (Security, System, Application) and PowerShell transcripts to the Splunk server over port 9997, as well as a custom index ad_index for AD specific events.
Log Sources and Ingestion
Key log sources included:
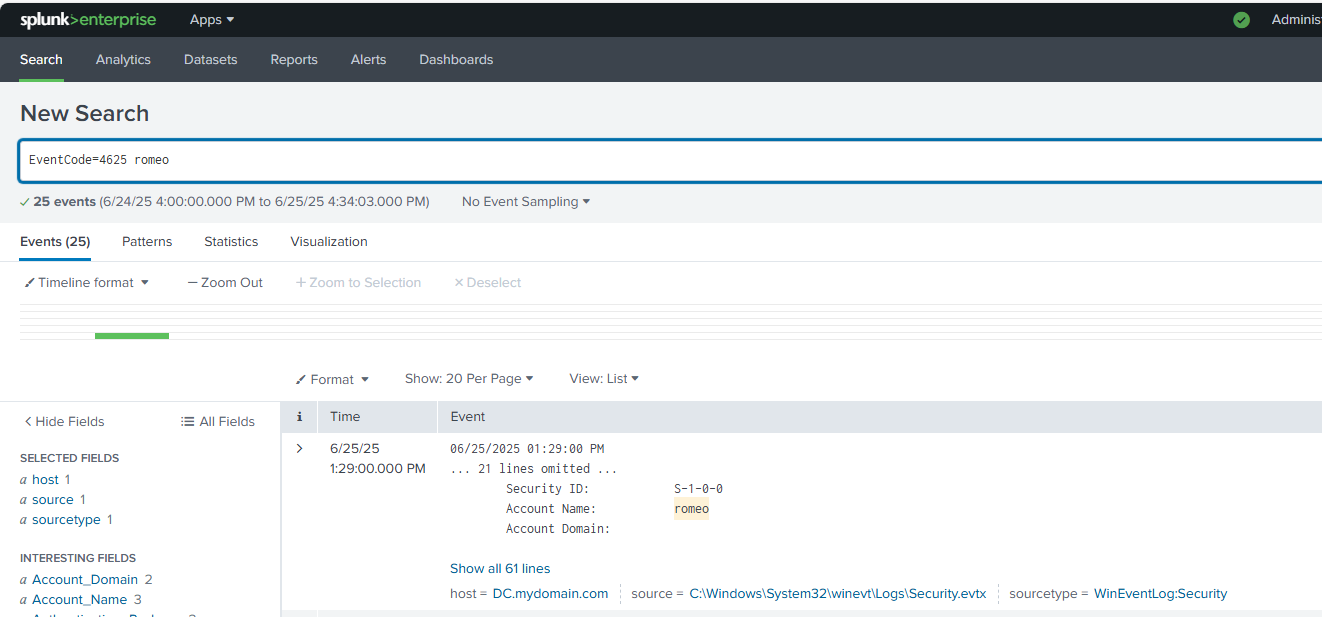
- Security logs (Event ID 4625 - failed logon attempts)
- PowerShell logs (command line auditing and execution)
- System logs related to reboots, service changes, and user logins
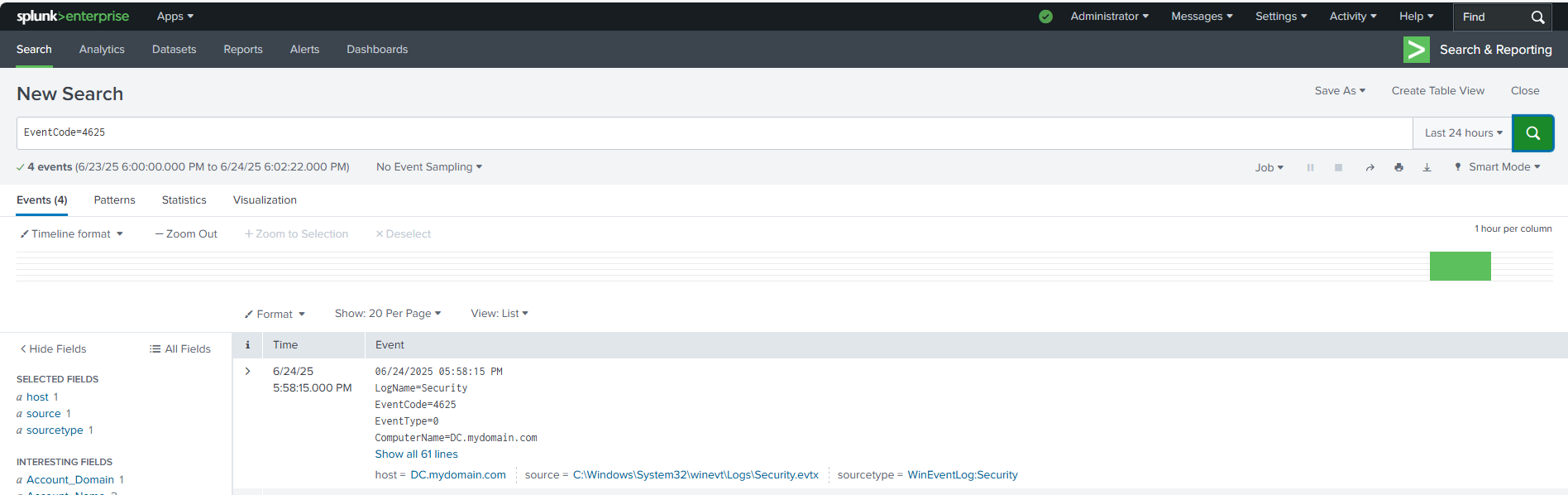
I tested the ingestion by performing failed logons and account lockouts from the Windows 10 client and searching the event logs for Event ID 4625.
Attack Simulation using Adversarial Techniques/Tools
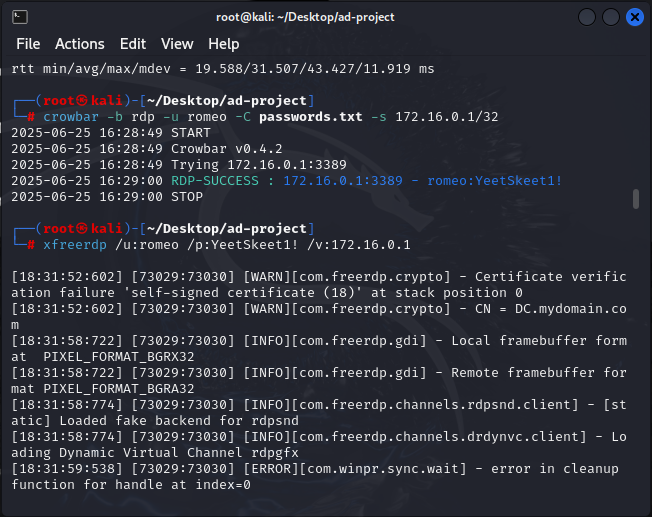
After setting up and testing Splunk on the DC machine, I went on the Kali Linux machine and started a simulated Active Directory attack on one of the users 'Romeo'. Using a tool called "Crowbar",
a credential brute-forcing automation tool, I attempted a brute force credential attack to RDP into the Romeo account using this command: crowbar -b rdp -u romeo -C passwords.txt -s 172.16.0.1/32
. I passed in a txt file of passwords to the tool with one of them being the correct one to simulate
a great number of logons in a small period of time to create that brute force attack, and result of the tool's execution showed the correct password and the successful RDP attempt, in which I RDP'd into Romeo's account
on the Kali Linux machine.
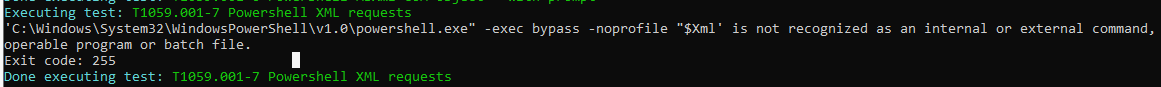
I used another tool called Atomic Red Team which is a MITRE ATT&CK-mapped framework of individual "atomic" tests. These tests simulate specific adversary techniques like PowerShell script execution which is what I
will be simulating as an attack on the DC machine. After installing Atomic Red Team on the DC machine, I executed this command: Invoke-AtomicTest T1059.001 which runs predefined simulated attacks that use
PowerShell maliciously.
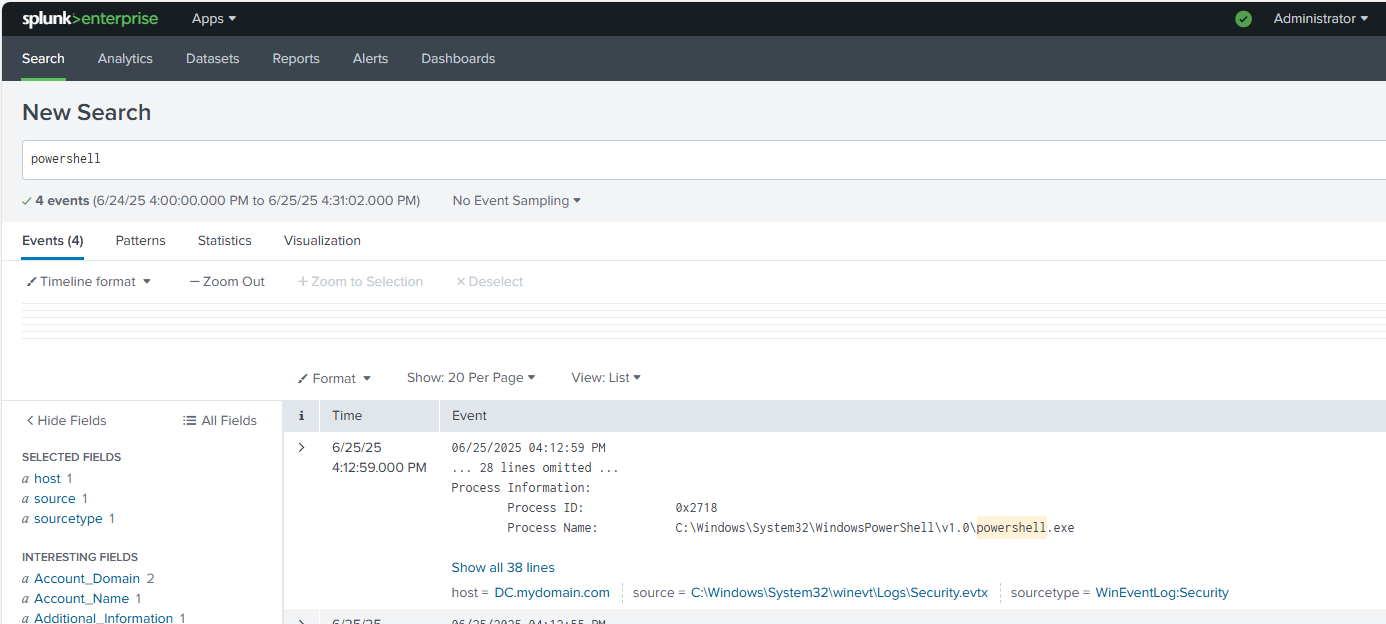
Below are the resulting logs from the subsequent attacks on the Active Directory environment. The screenshot on the left shows a log from the SPL query EventCode=4625 to return the failed logon attempts onto the 'Romeo' account.
The other screenshot shows the resulting logs from the Atomic Red Team simulated Powershell attack using the SPL query powershell.
Alert Creation in Splunk
After successfully ingesting Windows security logs of the simulated attacks into Splunk from my Domain Controller and endpoint machines using Universal Forwarders, I configured alerts to detect and respond to suspicious activity in real time.
One of the key alerts I created focused on monitoring failed login attempts, mapped to MITRE ATT&CK technique T1110 – Brute Force. Using EventCode=4625, I developed a Splunk query to detect when a single user account experiences more than five failed login attempts within a 10-minute window—indicative of a potential brute-force attack.
index=main EventCode=4625
| stats count by Account_Name, host
| where count > 5
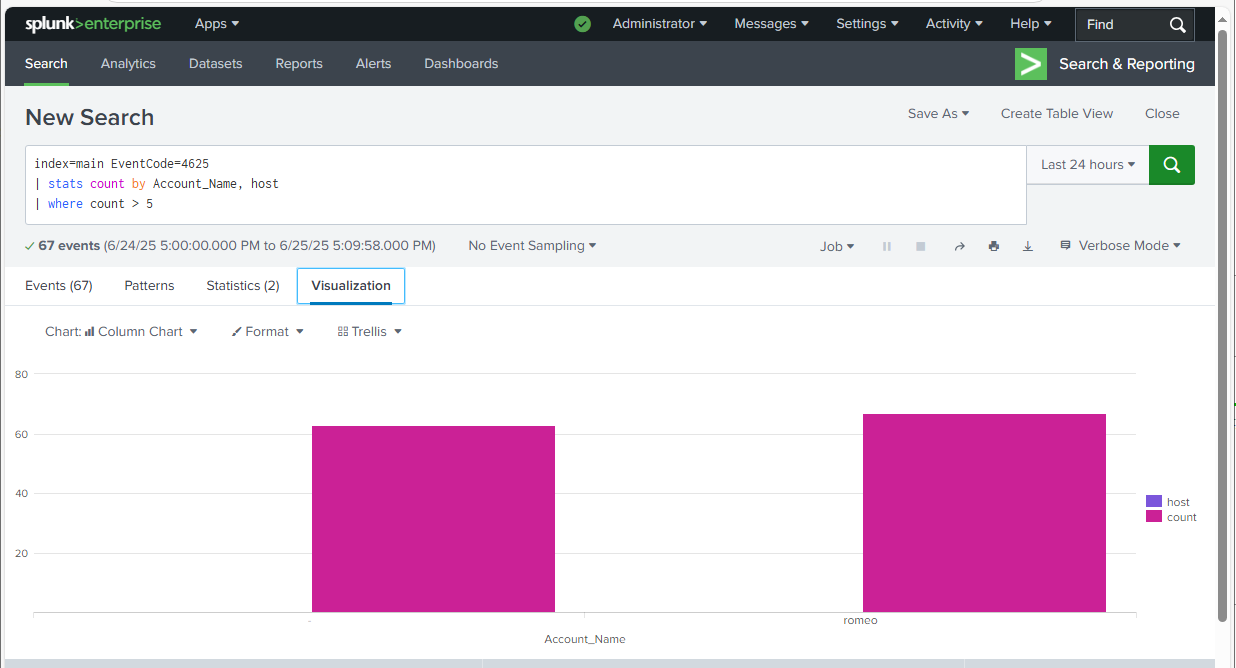
Once verified, I saved this query as a real time alert that triggers upon the attack. If triggered, the alert sends an email notification and can be configured to create a ticket or trigger a webhook in production environments.
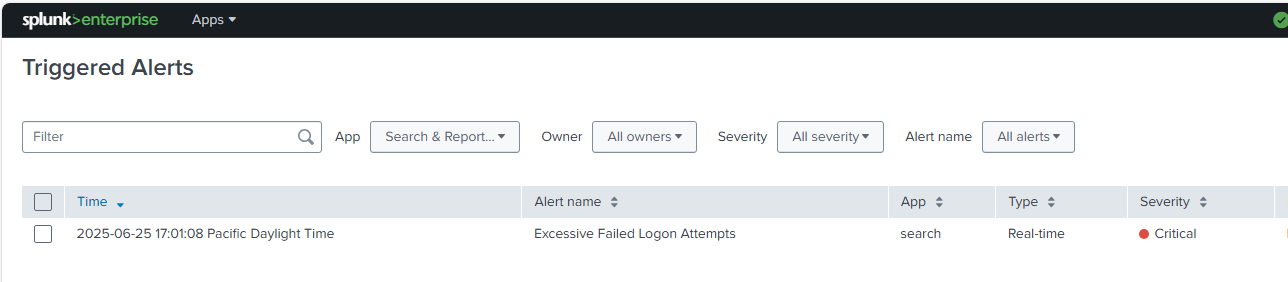
Alert Configuration Overview:
- Title: Excessive Failed Logon Attempts
- Alert Type: Real Time
- Trigger Condition: Number of results > 0
- Trigger Action: Email notification & Triggered Alert notification
Conclusion
This lab gave me hands-on experience deploying Splunk as a SIEM within an Active Directory environment. I configured log ingestion with Universal Forwarders, simulated real-world attacks using Crowbar and Atomic Red Team, and built alerts to detect brute-force and PowerShell-based threats. These exercises strengthened my understanding of Windows event logging, MITRE ATT&CK-mapped detection, and alert tuning. I plan to expand this lab further by adding more telemetry sources, different simulated attacks, advanced detection logic, and dashboard visualizations.
Skills Learned
- Splunk Enterprise installation and forwarder configuration
- Windows log collection via Universal Forwarder
- SPL queries for threat detection
- Creating dashboards and alert logic
- Analyzing and interpreting Windows Event Log data
Challenges Encountered
- Initial connectivity issues due to incorrect receiving port settings on the Splunk indexer
- Forwarders failing to send logs until service restarts and permissions were adjusted
- RDP connection attempts failing due to enabled account lockout settings in the domain